Underrated Ideas Of Info About How To Start A Dos Attack

Use it for educational purpose.
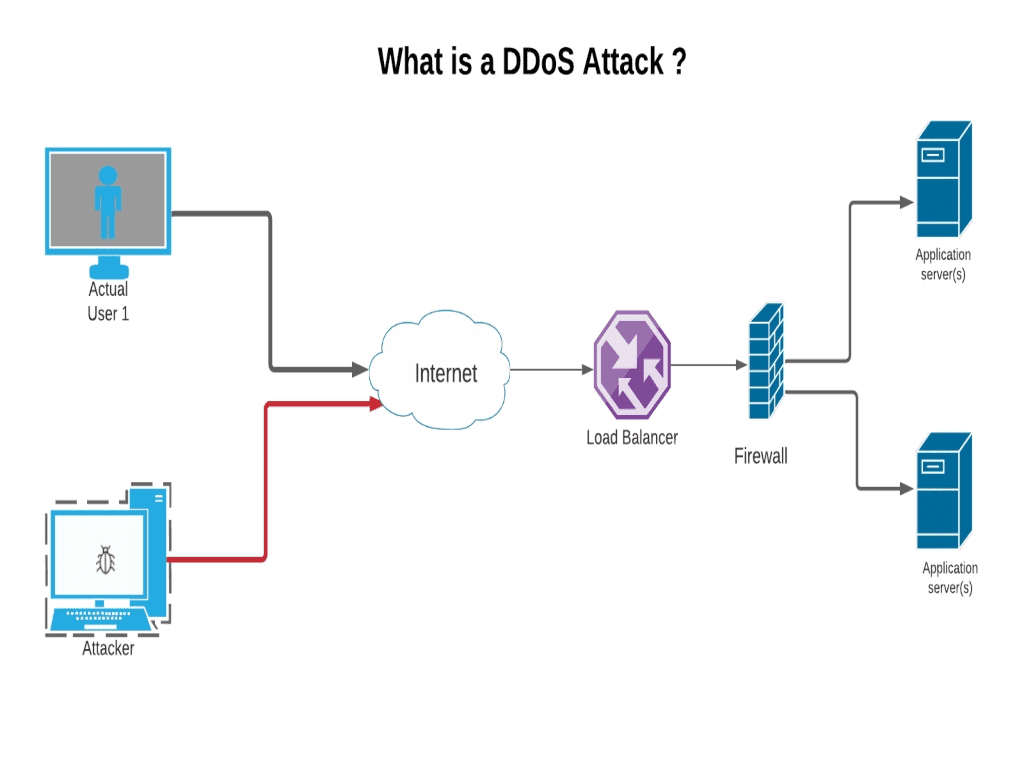
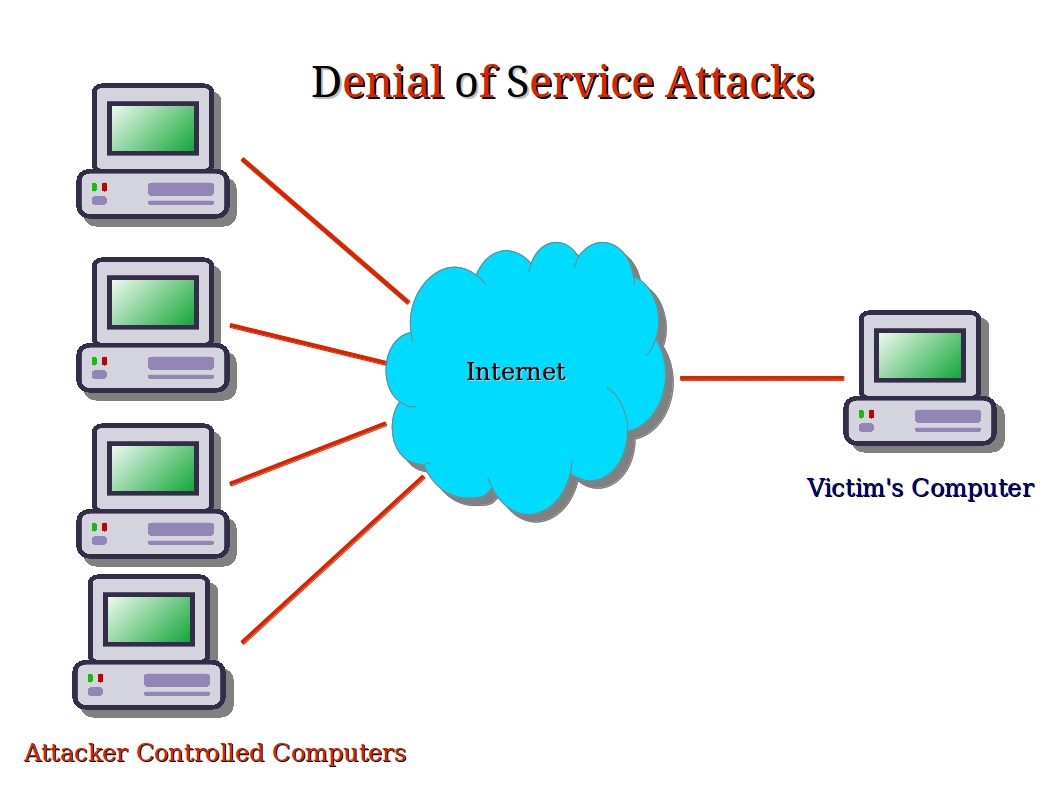
How to start a dos attack. Users and prompted federal investigations was not caused by a. To recap, there are a few key differences between ddos and dos attacks: I.e a single pc sends traffic to the target system.
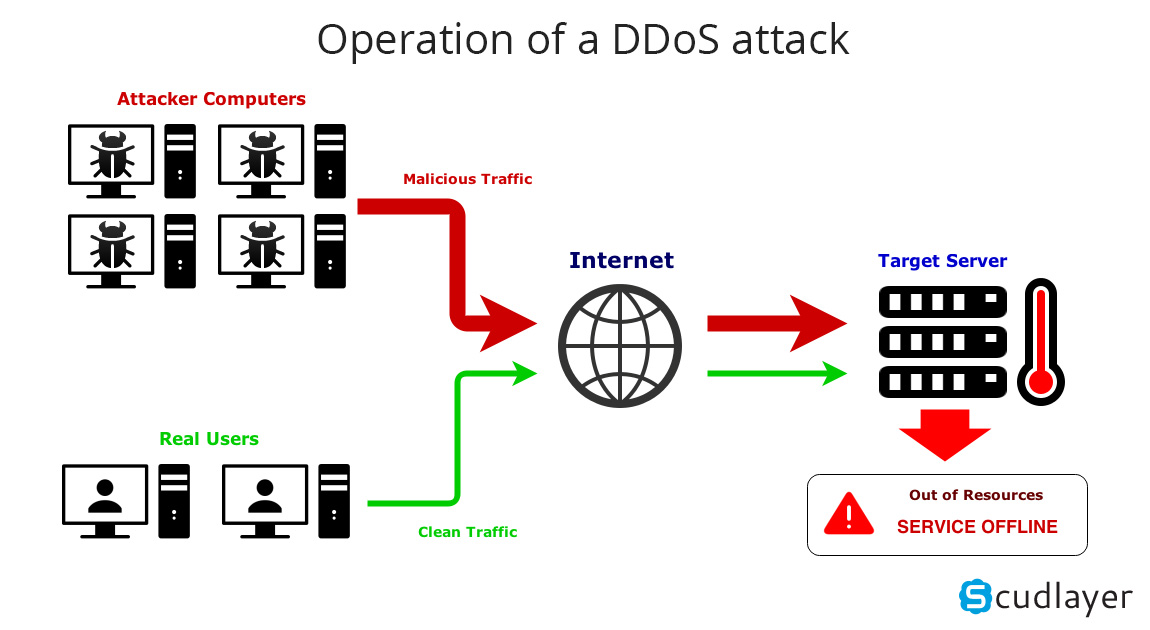
Attackers achieve this by sending more traffic than the target can handle,. A “denial of service” or dos attack is a deliberate shutting down of a network, website, or device in order to deprive the intended users from accessing them. Analyzing incoming traffic and determining whether or not it's.
Download and install the application the first thing you need is the software. Con colores contrastantes audaces, una. In this practical scenario, we are going to use nemesy to generate data packets and flood the target computer, router or server.
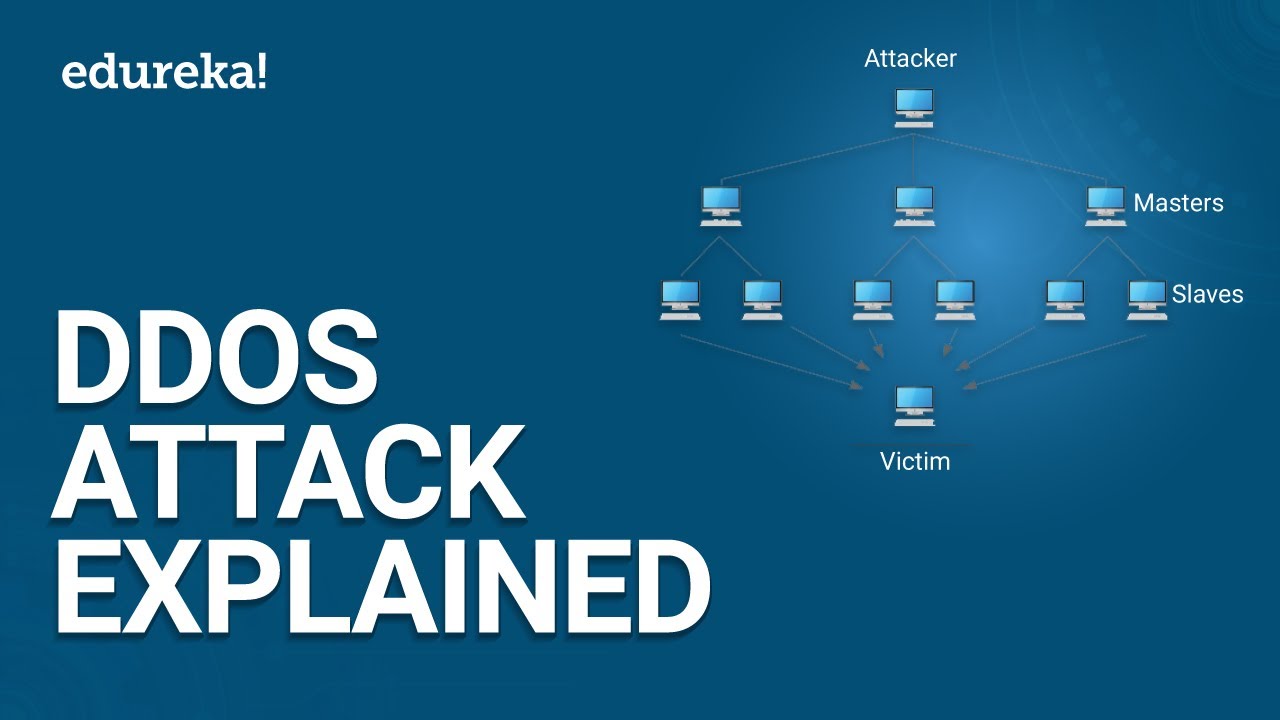
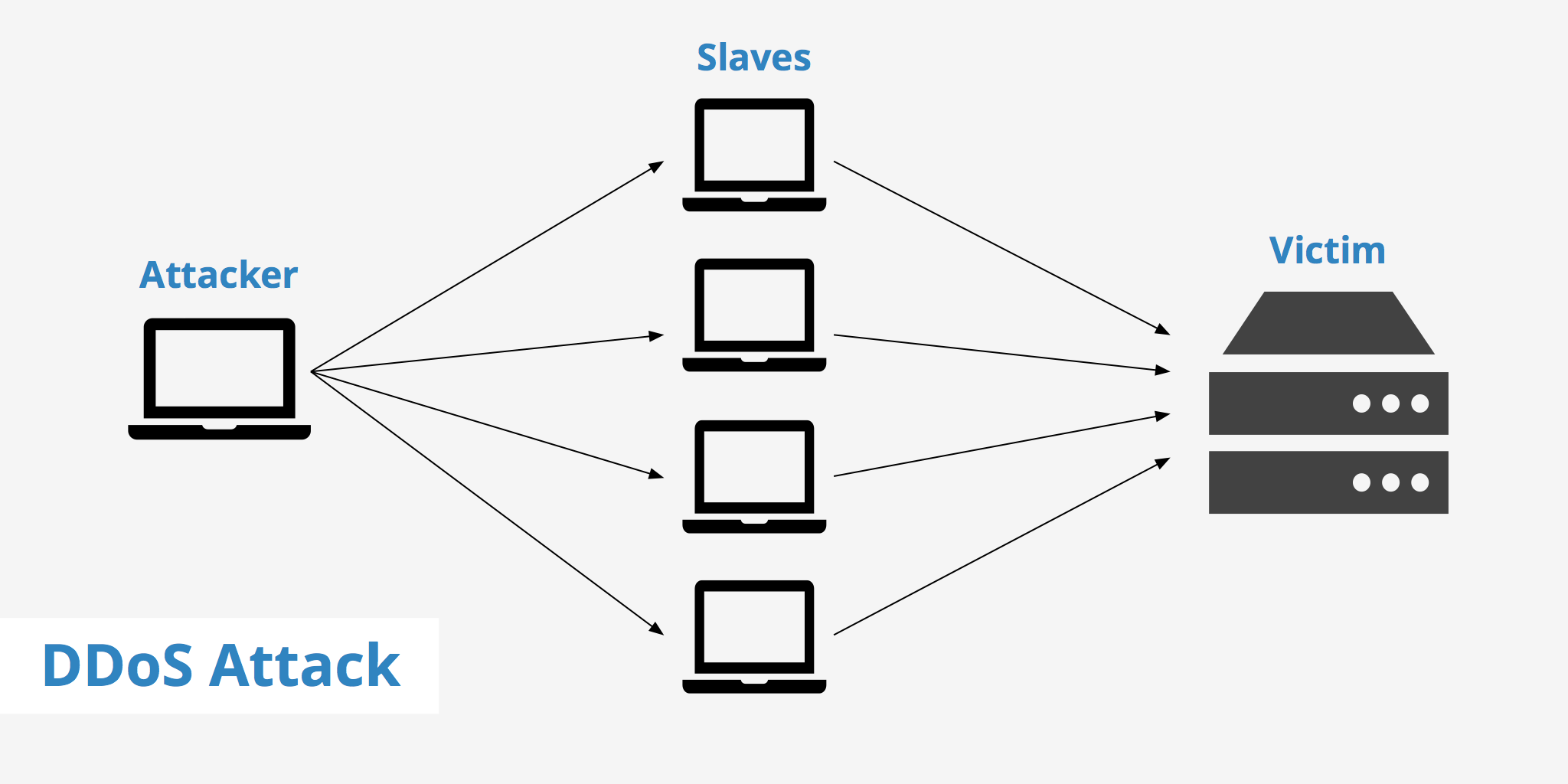
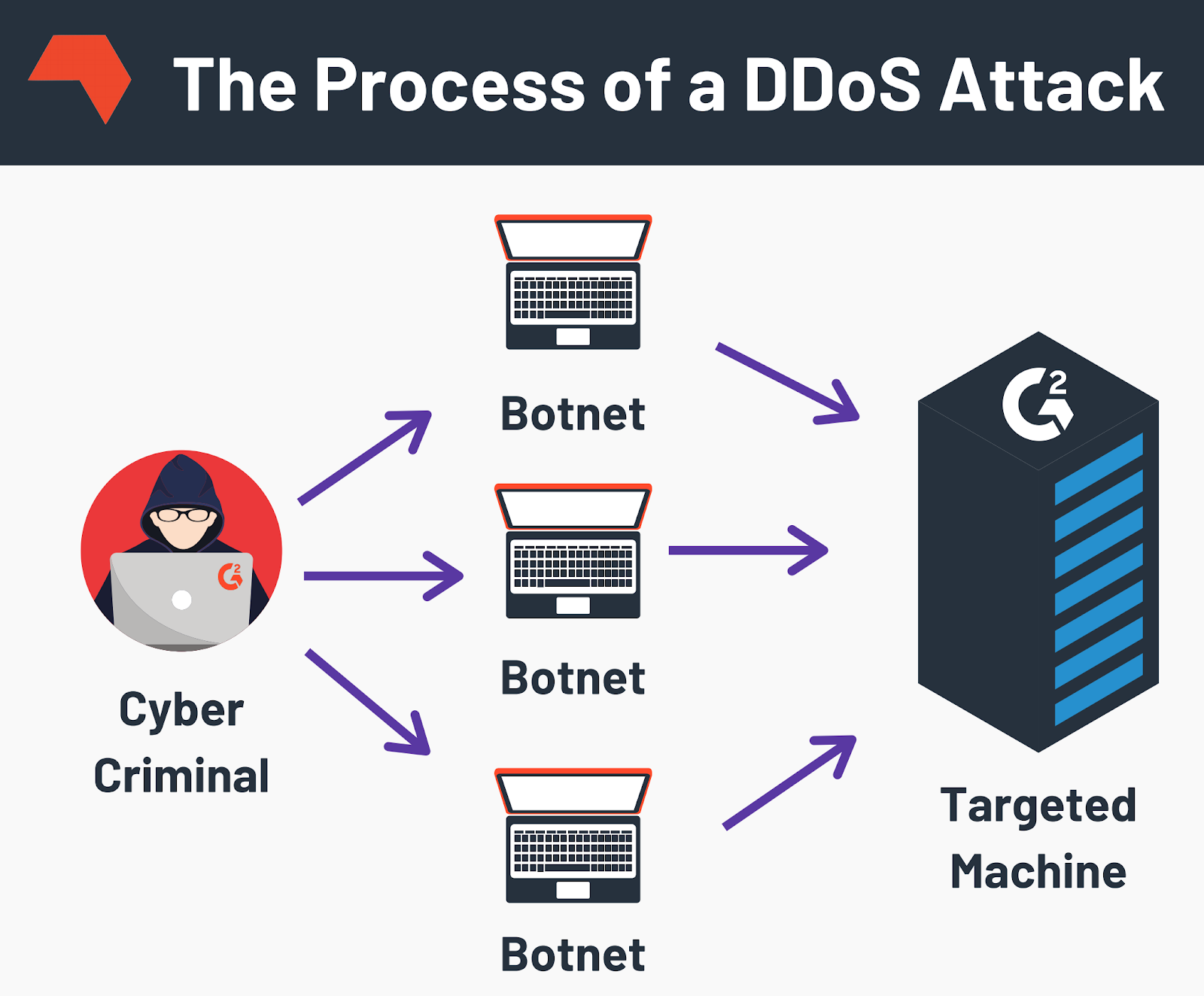
A ddos attack is a denial of service (dos) attack that uses a botnet to flood the target with malicious traffic. Diagram of a ddos attack. El equilibrio se encuentra más allá de los límites con esta copia exacta de un look famoso.
To see the effect of the ddos. El yin y el yang. Flooding the target with multiple malicious requests, or crashing the target by sending very large amounts of.
Launch a dos tool, like loic. Specify the ip address of the server you want to. Note how multiple computers are attacking a single computer.
After you select a service to target, follow these five steps to mount a dos attack: In the wake of israel’s devastating war on gaza, the jerusalem municipality has stepped up home demolitions on the east side of the city, which israel annexed from. A previous version of this article incorrectly asserted that, in leaked documents, the chinese hacking group isoon claimed to be able to exploit vulnerabilities in u.s.
La pasión de lo voluble. A denial of service attack’s intent is to deny legitimate users access to a resource such as a network, server etc. You can follow a step by step tutorial on how to launch bots using mirai botnet.
You can also see the effect of the ddos attack on the targeted website using the task manager and by viewing the network activities. The first step of any mitigation strategy is understanding when you are the target of a dos attack. At&t said late on thursday an outage that disrupted calls and text messages for thousands of u.s.
Mechanism of a denial of service (dos) attack on a network. Usually, this is done using one of two methods: There are two types of attacks, denial of.










![[dos attack rst scan] How to Change](https://arzhost.com/blogs/wp-content/uploads/2021/11/ACK-check-DOS-attack-work.jpg)